IMSI Catcher
Cell-Site Simulators/IMSI Catchers
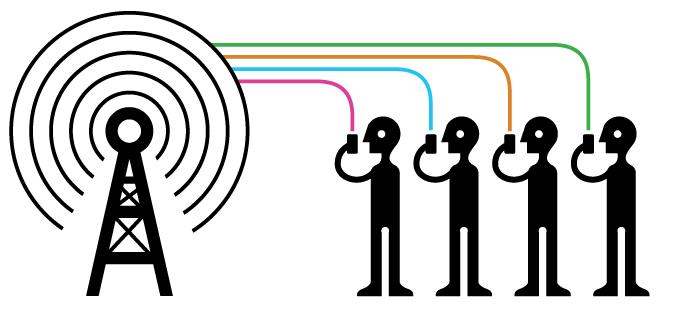
Cell-site simulators, also known as Stingrays or IMSI catchers, are devices that masquerade as legitimate cell-phone towers, tricking phones within a certain radius into connecting to the device rather than a tower.
Cell-site simulators operate by conducting a general search of all cell phones within the device’s radius, in violation of basic constitutional protections. Law enforcement use cell-site simulators to pinpoint the location of phones with greater accuracy than phone companies. Cell-site simulators can also log IMSI numbers (unique identifying numbers) of all of the mobile devices within a given area. Some cell-site simulators may have advanced features allowing law enforcement to intercept communications or even alter the content of communications.
Cell-Site Simulators/IMSI Catchers
STANDAARD COMMUNICATION
Cellular networks are distrubuted over geographic areas called “cells”. Each cel is served by one transceiver, also known as a cel-site or base station. Your phone naturally connects with the closest base station to provide you service as you move through various cells.
Generally, there are two types of device used by law enforcement that are often referred to interchangeably: passive devices (which we will call IMSI catchers), and active devices (which we will call cell-site simulators.) Passive devices, as a rule, do not transmit any signals. They work by plucking cellular transmissions out of the air, the same way an FM radio works. They then decode (and sometimes decrypt) those signals to find the IMSI of the mobile device and track it.
Active cell-site simulators work very differently from their passive cousins. Cellular devices are designed to connect to the cell site nearby with the strongest signal. To exploit this, cell-site simulators broadcast signals that are either stronger than the legitimate cell sites around them, or are made to appear stronger. This causes devices within range to disconnect from their service providers’ legitimate cell sites and to instead establish a new connection with the cell-site simulator. Cell-site simulators also have passive capabilities, such as identifying legitimate cell sites and mapping out their coverage areas. For the purposes of this article we will primarily discuss active cell-site simulators.
It is difficult for most people to know whether or not their phone’s signals have been accessed by an active cell-site simulator, and it is impossible for anyone to know if their phone’s signals have been accessed by a passive IMSI catcher. Apps for identifying the use of cell-site simulators, such as SnoopSnitch, may not be verifiably accurate. Some more advanced tools have been built, which may be more accurate.
What Kinds of Data Cell-Site Simulators Collect
Data collected by cell-site simulators can reveal intensely personal information about anyone who carries a phone, whether or not they have ever been suspected of a crime.
CELL-SITE SIMULATOR SURVEILLANCE
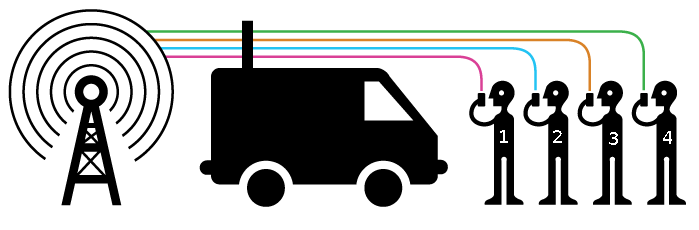
Cell-site simulators trick your phone into thinking they are base stations.
Depending on the type of cell-site simulator in use, they can collect the following information:
- Identifying information about the device like International Mobile Subscriber Identity (IMSI) number
- Metadata about calls like who you are dialing and duration of call
- Intercept the content of SMS and voice calls
- Intercept data usage, such as websites visited
Once your cellular device has connected to a cell-site simulator, the cell-site simulator can determine your location and read identifying data such as IMSI or ESN numbers directly from your mobile device. It can also intercept metadata (such as information about calls made and the amount of time on each call), the content of unencrypted phone calls and text messages and some types of data usage (such as websites visited). Additionally, marketing materials produced by the manufacturers of cell-site simulators indicate that they can be configured to divert calls and text messages, edit messages, and even spoof the identity of a caller in text messages and calls.
How Law Enforcement Uses Cell-Site Simulators
Police can use cell-site simulators to try to find a suspect when they already know their phone’s identifying information, or to scoop up data on anyone in a specific area. Some cell-site simulators are small enough to fit in a police cruiser, allowing law enforcement officers to drive to multiple locations, capturing from every mobile device in a given area—in some cases up to 10,000 phones at a time. These indiscriminate, dragnet searches include phones located in traditionally protected private spaces, such as homes and doctors’ offices.
Law enforcement officers have used information from cell-site simulators to investigate major and minor crimes and civil offenses. For example, they have used their devices for a wide variety of purposes, ranging from tracking a kidnapper to trying to locate a man who took his wife’s phone during an argument (and later returned it to her). Police have even deployed cell-site simulators at protests.
In US of America Cell-site simulators are used by the FBI, DEA, NSA, Secret Service, and ICE, as well as the U.S. Army, Navy, Marine Corps, and National Guard.
In Europe, all the equivalent organizations and agencies also use the cell-site simulator actively.
SPECIAL NOTICE: The above article/information is copied from the EFF (Electronic Frontier Foundation) in order to be able to translate it. The original can be found at this link.

