Security
The IT Security Chain
The more links in your network’s chain-databases, cloud-based servers, API’s and mobile applications- the more potential vulnerabilities you face. Here’s an overview of IT security to consider.
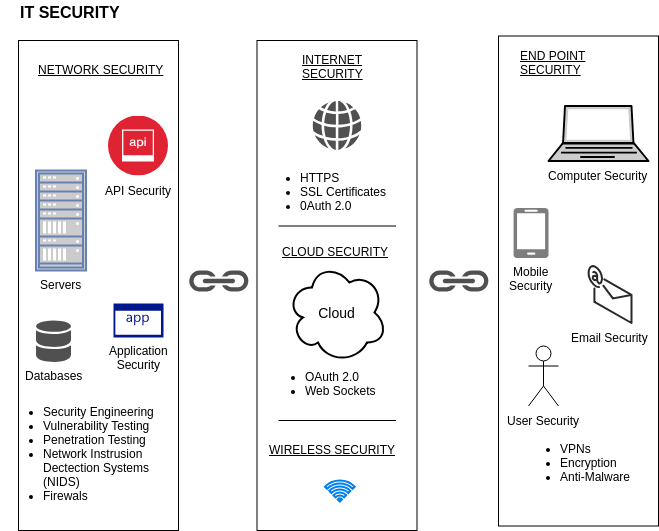
Why are there so many types of IT security? The more links in a network’s chain, the more opportunities for hackers to find their way in. Each component requires its own subsequent security measures—with many of them overlapping and working in tandem, much like the actual components of a network do.
It’s also important to note that with security, there’s no one-size-fits-all approach. Every network is different and requires skilled professionals to create tailored plans across all fronts: apps, databases, network devices, cloud servers, IT infrastructures, and the often weakest link in the security chain: users. These security plans are living, breathing things that need to be updated, upgraded, and patched on a constant basis, too.
NETWORK SECURITY: THE BEST DEFENSES
Security is anything you do to protect your network, both hardware and software. Network administrators (or system administrators) are responsible for making sure the usability, reliability, and integrity of your network remains intact. A hacker is capable of getting into a network and blocking your access, for example by holding a system hostage for a bitcoin ransom. You need an excellent defense in place to ensure you’re protected.
Detecting weaknesses in a network can be Network achieved through:
- Security engineering: the practice of protecting against these threats by building networks to be safe, dependable, and secure against malicious attacks. Security engineers design systems from the ground up, protecting the right things in the right ways. If a software engineer’s goal is to ensure things do happen (click here, and this happens), a security engineer’s goal is to ensure things don’t happen by designing, implementing, and testing complete and secure systems.
As a part of security engineering, there are proactive measures to predict where vulnerabilities might lie and reinforce them before they’re hacked:
- Vulnerability assessment: Engineers identify the worst case scenarios and set up proactive plans. With security analysis software, vulnerabilities in a computer, network, or communications infrastructure are identified and addressed.
- Penetration testing: This entails deliberately probing a network or system for weaknesses.
- Network intrusion detection systems (NIDS): This type of software monitors a system for suspicious or malicious activity.
Network admins are able to target threats (whether through suspicious activity or large queries to a database), then halt those attacks, whether they’re passive (port scanning) or active, like:
- Zero-day attacks, also called zero-hour attacks—attacks on software vulnerabilities that often occur before the software vendor is aware of it and can offer a patch. Or, hackers will initiate attacks on the software vulnerability the day that it’s made public there’s an issue, before users can install patches (hence the name “zero day”)
- Denial of service attacks
- Data interception and theft
- Identity theft
- SQL injection
Other methods of protecting networks include:
- IT Security frameworks: These act like blueprints for a company to set up processes and policies for managing security in an enterprise setting. Which a company uses can depend on the industry and compliance requirements.
- Password “salt and peppering”: Adding a salt, or random data, to a password makes common passwords less common. A pepper is also a random value attached to the password, which is helpful in slowing hackers down.
- Authorization, authentication, and two-factor authentication (sometimes sent via SMS, although this can prove vulnerable as well)
- Virtual Private Networks (VPNs)
- Application whitelisting, which prevents unauthorized apps from running on a computer
- Firewalls: Block unauthorized access to a network or data interceptions
- Honeypots: These are like decoy databases that attract hackers but don’t house any important information.
- Anti-virus software
- Encryption—decoding data, in transit or at rest, including end-to-end encryption often used in messaging apps and platforms that only allows encrypted messages to be read by sender and receiver
Within network security is also content security, which involves strategies to protect sensitive information on the network to avoid legal or confidentiality concerns, or to keep it from being stolen or reproduced illegally. Content security largely depends on what information your business deals in.
ENDPOINT SECURITY: SECURING THE WEAKEST LINK
It’s said that users are often the weakest link in the security chain, whether it’s because they’re not properly educated about phishing campaigns, mistakenly give credentials to unauthorized users, download malware (malicious software), or use weak passwords. That’s why endpoint security is so crucial—it protects you from the outside in.
Endpoint security technology is all about securing the data at the place where it both enters and leaves the network. It’s a device-level approach to network protection that requires any device remotely accessing a corporate network to be authorized, or it will be blocked from accessing the network. Whether it’s a smartphone, PC, a wireless point-of-sale, or a laptop, every device accessing the network is a potential entry point for an outside threat. Endpoint security sets policies to prevent attacks, and endpoint security software enforces these policies.
If you’ve ever accessed a network through a virtual private network (VPN), you’ve seen endpoint security in action. Malware is one of the core threats addressed by endpoint security, including remote access trojans (RATs), which can hack into a laptop and allow hackers to watch you through your webcam.

